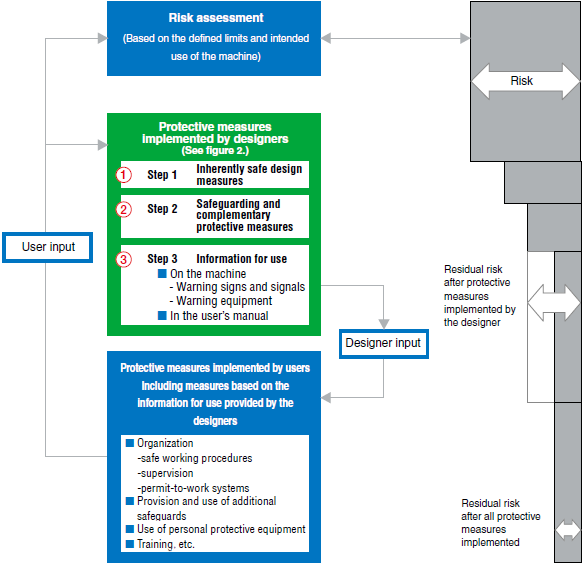
3-step Method
3-step Method and Protective Measures
What are protective measures?
These are measures designed with the purpose of achieving risk reduction. Protective measures can be separated into two major groups: protective measures implemented by designers and protective measures implemented by users.
What is the 3-step Method?
These are three methods implemented by designers and are
classified as shown below.
- 1.Inherently safe design measures
- 2.Safeguarding and complimentary protective measures
- 3.Information for use
According to priority, these measures are ordered as 1, 2, and then 3. In other words, it is desirable to implement measures according to the following procedure, which is
called the 3-step Method and protective measures.
- Protective Measures, from ISO 12100:2010
- The following definition applies.
Measure intended to achieve risk reduction, implemented - by the designer (inherently safe design, safeguarding and complementary protective measures, information for use) and/or- by the user(organization: safe working procedures, supervision, permitto-work systems; provision and use of additional safeguards; use of personal protective equipment; training)
- Complimentary protective measures, from ISO 12100:2010
- Protective measures which are neither inherently safe design measures, nor safeguarding (implementation of guards and/or protective devices), nor information for use, could have to be implemented as required by the intended use and the reasonably foreseeable misuse of the machine.
- Inherently safe design measures,
from ISO 12100:2010
- The following definition applies.
Protective measures which either eliminates hazards or reduces the risks associated with hazards by changing the design or operating characteristics of the machine without the use of guards or protective
devices
- Information for use, from ISO 12100:2010
- The following definition applies.
Protective measure consisting of communication links (for example, text, words, signs, signals, symbols, diagrams) used separately or in combination, to convey information to the user.
- Safeguarding, from ISO 12100:2010
- The following definition applies.
Protective measures using safeguards to protect persons from the hazards which cannot reasonably be eliminated or risks which cannot be sufficiently safe design measures
- Residual risk, from ISO 12100:2010
- This is the risk remaining after protective measures have been implemented.
ISO 12100: 2010 distinguishes 1) the residual risk after protective measures have been implemented by the designer, and 2) the residual risk remaining after all protective measures have been implemented.
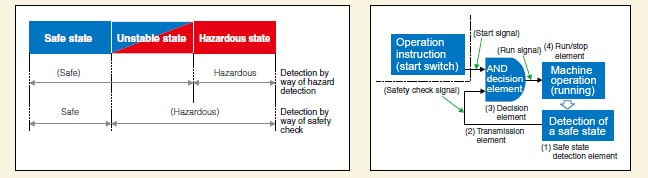
- Safety confirmation systems
-
These systems only permit the operation of a machine after safety has been confirmed. This is a method for constructing definite safety. In detail, it can be said the starting and running of machines is permitted by these systems only when they detect the absence of users in the operation range of the machine.
Example of Implementing the 3-step Method and Protective Measures

Let’s examine each step of the protective measures according to the risk
assessment flowchart and the 3-step Method and protective measures.
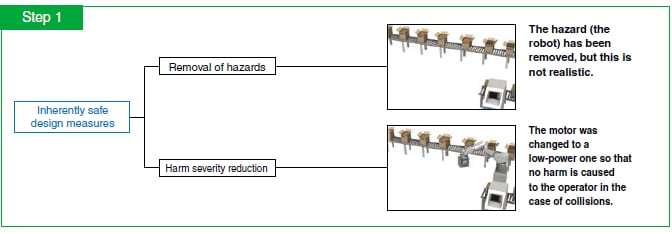
The inherently safe design measures represent the first step, are the only way to remove hazards, and are the most effective way to reduce risk.
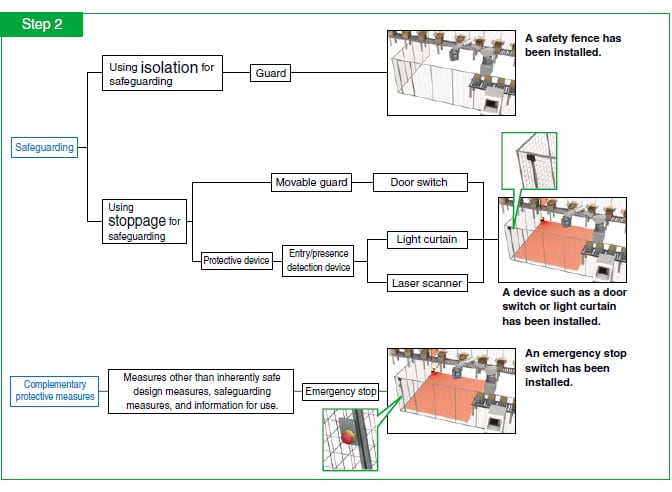
The next measure is the implementation of safeguards. This measure is required when the risks are not sufficiently reduced by way of the inherently safe design measures. Safeguards are normally classified into two groups.
Safeguarding by way of isolation and by way of stopping. For the former, guards (protective fences) are most commonly used. For the latter, light curtains or laser scanners are used as one method. Complementary protective measures (for example, emergency stop switches) are measures that differ from inherently safe design measures, safeguarding, and information for use and that are necessary due to risk existing because of the intended use and the reasonably foreseeable misuse of the machine. In the 3-step Method, these measures are positioned in step 2 together with safeguarding. An example of these complementary protective measures is an emergency stop device.
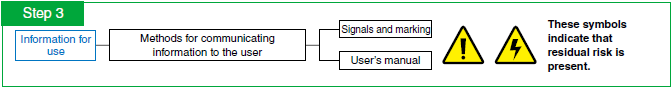
The last step is the provision of information for use. This is the final method and is required when risk cannot be removed or reduced by way of the inherently safe design measures, and safeguarding and complementary protective measures described above.
- Intended use of machine
- This is the use of the machine based on the information provided within the instructions for use.
Examples include the ways of using the machine as described in its user’s manual or catalog (using the machine as intended by its designers).
- Reasonably foreseeable misuse
- This refers to uses of the machine unintended by the designers and that arise from easily foreseeable human behavior.
[Example 1] Using a machine with the door switch disabled and the door opened in order to improve takt time.
[Example 2] Attempting to remove a component by inserting your hand into the
drive part while the machine is operating.
- Emergency stop
- This is an emergency action that stops the processes or operation of the machine in dangerous situations. ISO 13850 defined the following two points.
- It must avert arising, or reduce existing,
hazards to persons, damage to machinery or
to work in progress.
- It must be initiated by a single human action.





